

Pre Account Take is an interesting vulnerability that most people don’t know about. It only occurs under strict circumstances but when exploited it leads to account take over. If a site doesnt have email verification an attacker can sign up using a targets email before the target does. If the target later signs up for the application using single sign on(SSO) their account will be linked to the attacker's account.
As mentioned earlier the application needs to let you sign up without verifying your email. Normally applications require you to verify you own the email used to sign up by sending you a link to click on. If the application fails to do this then you would be able to create an account using any email you want, even if you own it.

If you see something like the image above then you are required to verify your email before signing up. That means the site won’t be vulnerable to the pre account takeover vulnerability.
Some applications have two ways of signing up such as SSO and manually creating an account. You can tell because when you go to the signup or creat account page you will see two options as shown in the image below:

As you can see you can manually create an account by typing in your email and password or you can just click the google SSO button. That may seem fine but what happens when you create an account manually and then later try to sign in using SSO.
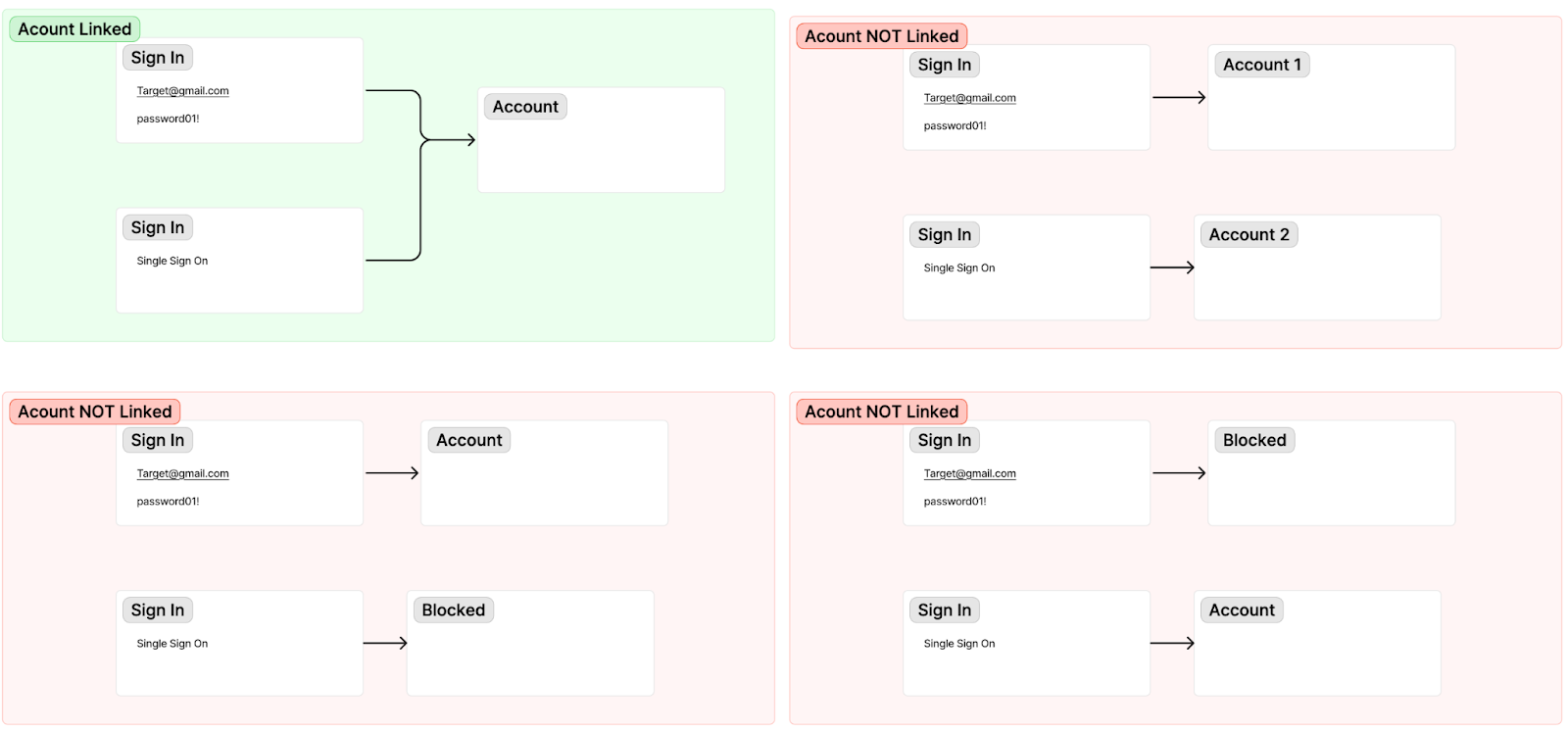
Some applications don’t allow that and will force you to sign in using the email/password. However, other applications will link the SSO account to the account that was already created. When this happens you can use both your email/password you created and SSO to login to the application.
In order to pull off this exploit the site must first have email verification disabled. If that is disabled the account that is created manually must be linked to the same account the SSO account is linked to. If those two things are true then the application is vulnerable.

The attack works by first manually creating an account using the target's email address. Later if the target goes to create an account or login using SSO they will be linked to the same account. That means that you will be able to access the target account via the credentials you set up earlier . Its basically a backdoor that allows you to take over the account the SSO user is logged into.
This is a neat attack but it requires a lot of things to align. First the application has to be missing email verification. Second it has to link the manual and sso accounts together. Third, the target has to sign in using SSO. Since the attack requires the target to sign in and only use SSO this type of attack might not be as impactful. That being said its still a vulnerability and can be used to take over other users accounts granted they login via SSO.
Pre account takeover is one of those rare bugs that feels more like a trick than a hack but if the conditions are right, it can lead to a full account compromise. It’s not always high impact, but when it works, it’s clean, subtle, and dangerous. Keep an eye out for sites that skip email verification and allow SSO linkage you might just find yourself with a solid finding.
